Over two-thirds of people reuse passwords across websites, resulting in an increasingly insecure ecosystem.
Organizations lose millions of dollars annually and place themselves and their customers at high risk due to password-based authentication that is inherently unsafe delivers poor user experience and leaves customers unsatisfied and places brands at risk of jeopardizing their reputations. Research shows 55% of consumers stop using a website because the login process is too complex, while 87.5% find themselves locked out of an online account after too many failed login attempts. Even worse, 92% of consumers will completely abandon a website without completing a purchase instead of going through the steps to recover or reset login credentials. ~businesswire
While eliminating the password has obvious security benefits, the dramatic positive change in the user experience is often overlooked.
Your customers already have to remember too many passwords, which need to be longer and more complicated to supposedly keep hackers at away (spoiler alert: it doesn’t). Poor password habits, such as reusing a password across multiple sites, are behavior that comes about because of this annoying friction. The appeal of finding a powerful alternative to the password is powerful. Many tech leaders continue to seek and develop solutions. The FIDO Alliance has developed an alternative authentication system that will eliminate complex passwords that are difficult to remember.
What is the FIDO Alliance and Authentication?
It’s a group of tech giants, like Microsoft, Apple, and Google , who are working to create a new, more convenient and secure authentication standard. The acronym of the organization’s name sums it up very well: Fast IDentity Online. Its goal is to imagine a world without passwords.
The principle is to no longer have a password that can be forgotten or hacked using pernicious solutions such as phishing, installation of malicious software, hacking of data on servers, etc. FIDO plans to use cryptographic keys – called passkeys – as well as biometrics. Big advantage: these keys would never leave a person’s device and would be uniquely linked to a key on the server of the service in question.
The whole purpose of the FIDO Alliance is to define specifications and certifications interoperable with the hardware and mobile authenticators of many manufacturers and suppliers.
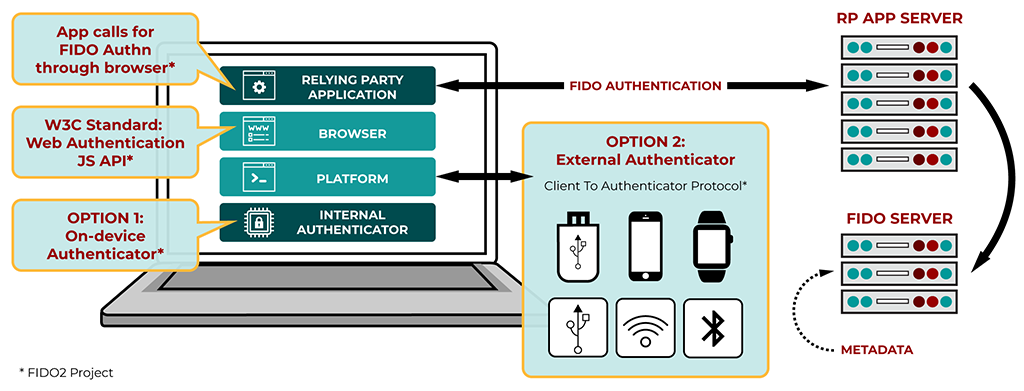
How does the FIDO protocol actually work?
It is based on a FIDO2 protocol, which uses public key cryptography. “ Public key infrastructure (PKI) was developed primarily to support secure information exchange over insecure networks,” says Gartner. It is a Client to Authenticator Protocols (CTAP) combined with the Web authentication protocol (WebAuthn) of the World Wide Web Consortium (W3C) so that it is compatible with a maximum amount of platforms.
By combining this protocol with the biometric systems of the latest generation devices, we obtain authentication without a password, but just as secure, if not more so. And, ultimately, a much smoother user experience.
Let’s take look at an example to better understand the process.
Imagine a consumer carrying out transactions with his bank via the mobile application installed on his phone. “Communication between the bank’s server and the customer’s phone must be encrypted. This is done using cryptographic keys, called a private and public key pair. Think of these PKI keys as locking and unlocking encrypted private information about the banking transaction. The public key is registered with the online service, for example, a bank’s server. The client’s private key can only be used after it has been unlocked on the device by the user. Therefore, cybercriminals have no server-side secrets to steal.
All the keys installed on the terminal can be saved in the cloud in order to be applied on a new device. By combining this protocol with the biometric systems of the latest generations of devices, we obtain authentication without a password, but just as secure, if not more so. And, ultimately, it provides a much smoother user experience, whether on your browser or on your application. Whether you broke your smartphone or want to change your computer, the FIDO Alliance has you covered. All the keys installed on the terminal can be saved in the cloud in order to be applied to a new device and thus facilitate the transition without having to start all over again.
All of this can be achieved through new technology players becoming members of the Alliance. In addition to Microsoft, Apple and Google, which we have already mentioned, Facebook, Amazon, Arm, Intel, Qualcomm and Samsung are also part of the consortium.
Software companies have been working hard to find solutions to the password crisis.
Companies like Scute provide a better way to secure software for an organization. Scute makes it easy for everyone in your company to access your systems and resources without friction. Executives, managers, engineers, peers, and consumers — all easily managed by one tool. With its meticulous design and robust architecture, Scute strengthens your company’s security while making it faster and more delightful for consumers and employees to access your systems and resources from anywhere.
Scute.io brings a passwordless experience and frictionless authentication that users will love.
More from NANO
Building Effective Marketing Strategies for Jewelry Brands
Building Effective Marketing Strategies for Jewelry Brands Marketing is fundamentally about creating and nurturing relationships. For jewelry brands, this involves two primary types of marketing: audience building and customer relationship building....